爱加密特性
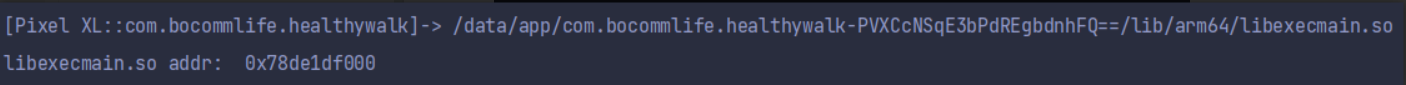
核心检测代码均在libexecmain.so中,爱加密会对该so进行加密处理,运行时会对其进行解密并释放到内存中,因此其基址会发生改变。
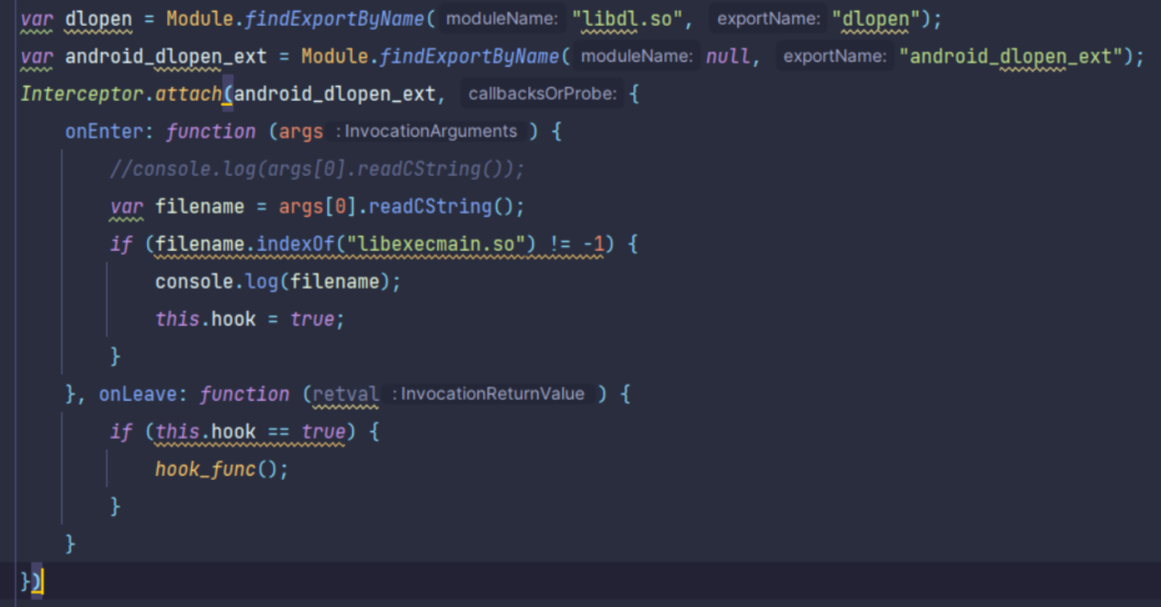
hook dlopen
因为基址会变化,因此需要在so加载的时候hook。
dump_so
获取到so的基址后从内存中读取so内容并写入sdcard目录下
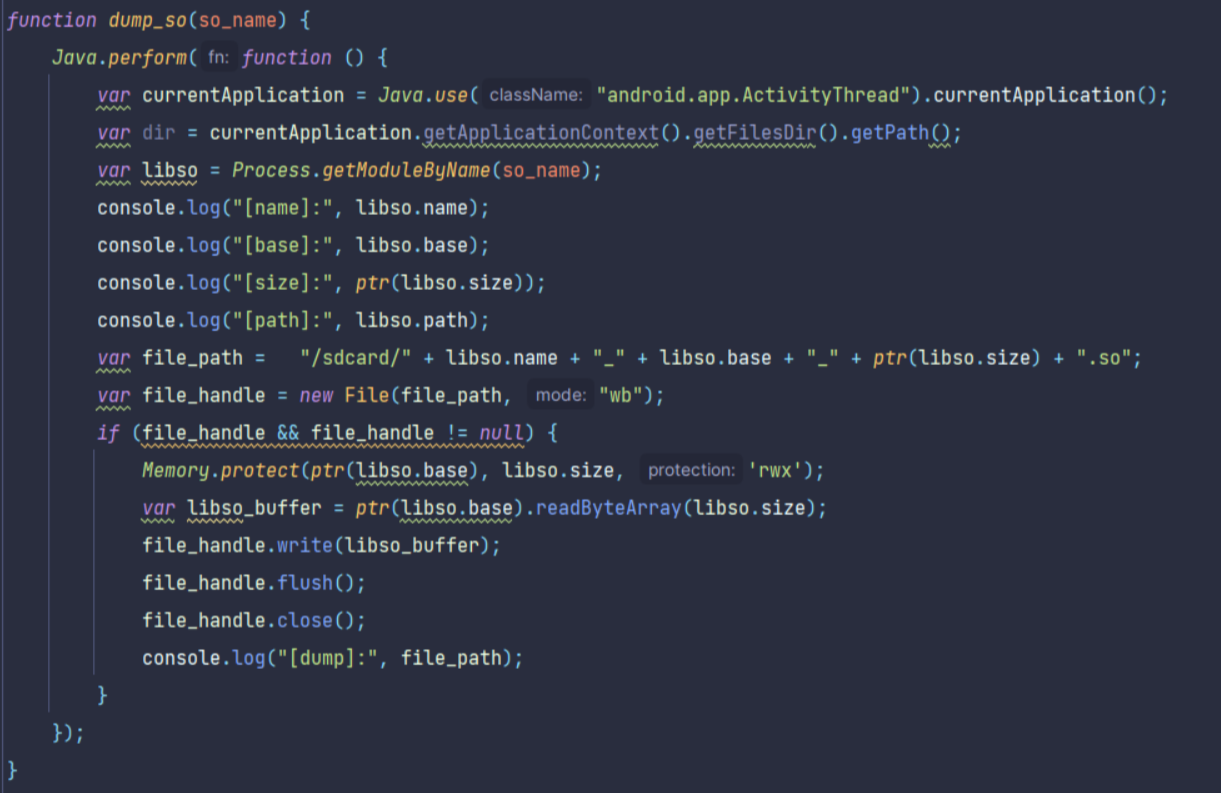
完整代码如下:
function dump_so(so_name) {
Java.perform(function () {
var currentApplication = Java.use("android.app.ActivityThread").currentApplication();
var dir = currentApplication.getApplicationContext().getFilesDir().getPath();
var libso = Process.getModuleByName(so_name);
console.log("[name]:", libso.name);
console.log("[base]:", libso.base);
console.log("[size]:", ptr(libso.size));
console.log("[path]:", libso.path);
var file_path = "/sdcard/" + libso.name + "_" + libso.base + "_" + ptr(libso.size) + ".so";
var file_handle = new File(file_path, "wb");
if (file_handle && file_handle != null) {
Memory.protect(ptr(libso.base), libso.size, 'rwx');
var libso_buffer = ptr(libso.base).readByteArray(libso.size);
file_handle.write(libso_buffer);
file_handle.flush();
file_handle.close();
console.log("[dump]:", file_path);
}
});
}
function hook_func() {
var soAddr = Module.findBaseAddress("libexecmain.so");
console.log("libexecmain.so addr: ", soAddr);
dump_so("libexecmain.so");
}
var dlopen = Module.findExportByName("libdl.so", "dlopen");
var android_dlopen_ext = Module.findExportByName(null, "android_dlopen_ext");
Interceptor.attach(android_dlopen_ext, {
onEnter: function (args) {
//console.log(args[0].readCString());
var filename = args[0].readCString();
if (filename.indexOf("libexecmain.so") != -1) {
console.log(filename);
this.hook = true;
}
}, onLeave: function (retval) {
if (this.hook == true) {
hook_func();
}
}
})内容明显变大,但后续仍需修复
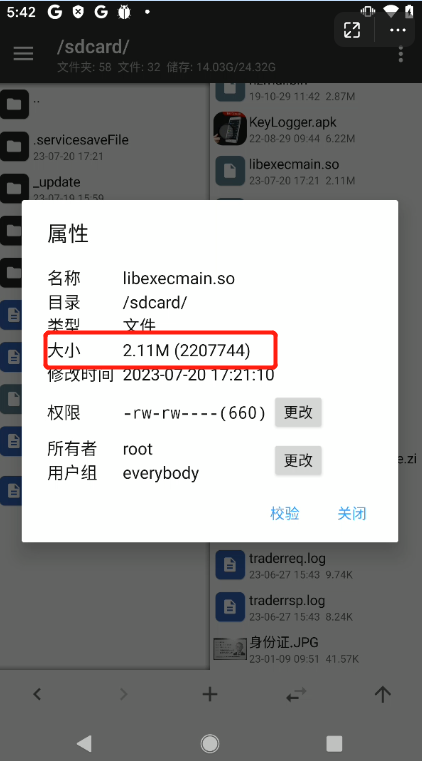
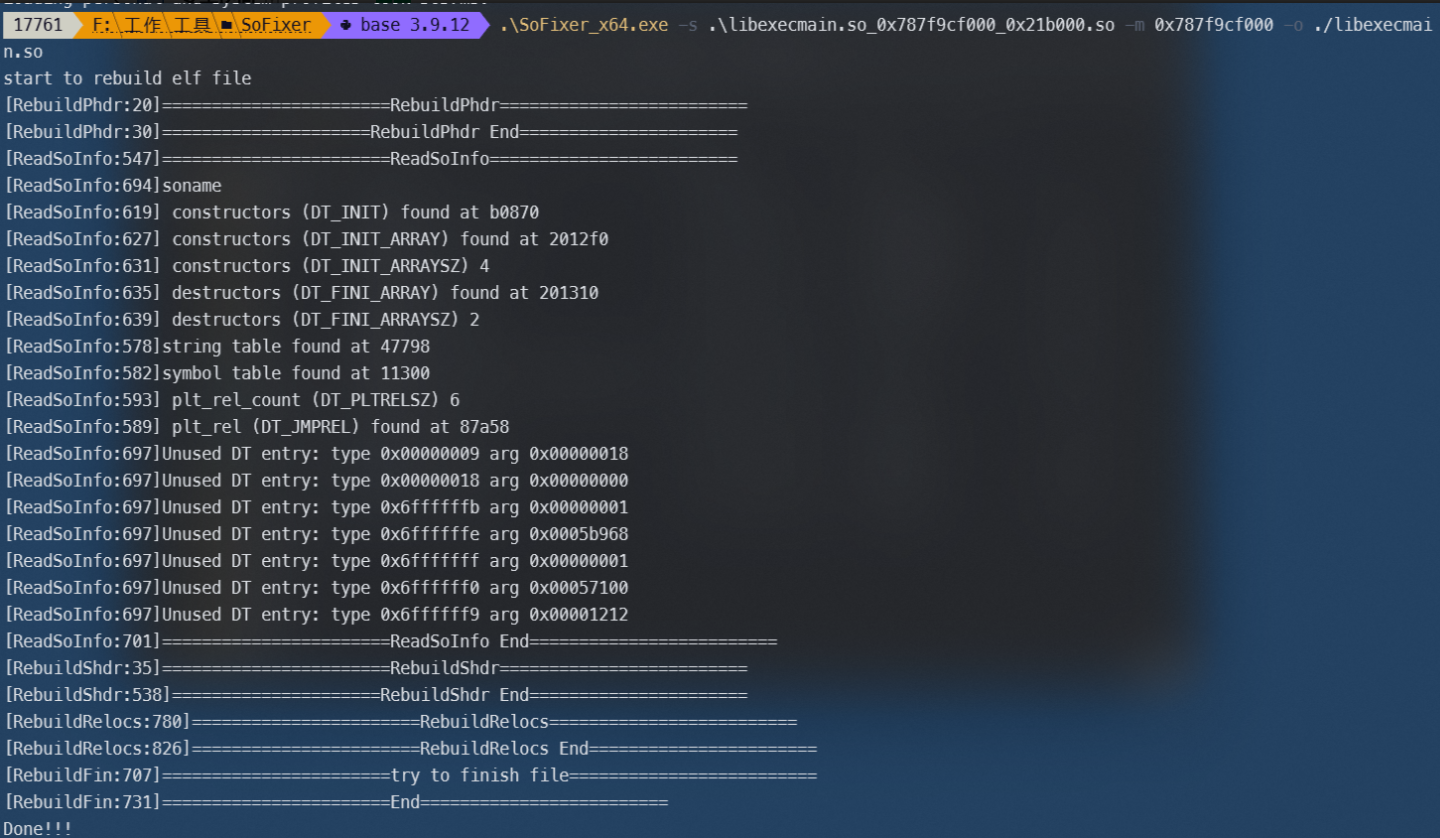
so修复
使用SoFixer即可完成对so的修复